ADCAIJ: Advances in Distributed Computing and Artificial Intelligence Journal
Regular Issue, Vol. 12 N. 1 (2023), e30632
eISSN: 2255-2863
DOI: https://doi.org/10.14201/adcaij.30632
Enhancing Energy Efficiency in Cluster Based WSN using Grey Wolf Optimization
Ashok Kumar Rai1, Lalit Kumar Tyagi2, Anoop Kumar3, Swapnita Srivastava4, Naushen Fatima5
1 Computer Science and Engineering Department, Madan Mohan Malviya University of Technology, Gorakhpur, UP, India, 2730010
2, 3 Computer Science and Engineering, Banasthali Vidyapith, Tonk-Newai, Rajasthan, India
4 School of Computer Science and Engineering, Galgotias University, Greater Noida
5 School of Computer Science and Engineering, Lovely Professional University, Phagwara, India
ashok7086@gmail.com, tyagilalit70@yahoo.co.in, anupbhola@banasthali.in, swapnitasrivastava@gmail.com, nausheen.28838@lpu.co.in
ABSTRACT
Wireless sensor networks (WSNs) are typically made up of small, low-power sensor nodes (SNs) equipped with capability for wireless communication, processing, and sensing. These nodes collaborate with each other to form a self-organizing network. They can collect data from their surrounding environment, such as temperature, humidity, light intensity, or motion, and transmit it to a central base station (BS) or gateway for additional processing and analysis. LEACH and TSEP are examples of cluster-based protocols developed for WSNs. These protocols require careful design and optimization of CH selection algorithms, considering factors such as energy consumption, network scalability, data aggregation, load balancing, fault tolerance, and adaptability to dynamic network conditions. Various research efforts have been made to develop efficient CH selection algorithms in WSNs, considering these challenges and trade-offs. In this paper, the Grey Wolf Optimization (GWO) algorithm is employed to address the problem of selecting CHs (CHs) in WSNs. The proposed approach takes into account two parameters: Residual Energy (RE) and the distance of node (DS)s from the BS. By visualizing and analyzing the GWO algorithm under variable parameters in WSNs, this research identifies the most appropriate node from all normal nodes for CH selection. The experimental results demonstrate that the proposed model, utilizing GWO, outperforms other approaches in terms of performance.
KEYWORDS
base station; cluster head; energy efficiency; grey wolf optimization; wire sensor network
1. Introduction
WSNs have emerged as a powerful and versatile technology with applications spanning various domains, including environmental monitoring, industrial automation, healthcare, and smart cities. WSNs are made up of small SNs equipped with sensing, computing, and wireless communication capabilities, enabling them to collaboratively gather and disseminate valuable information about the physical environment.
The proliferation of WSNs has been driven by the need for cost-effective, real-time data collection and monitoring in diverse scenarios. These networks offer unique advantages over traditional wired systems, such as ease of deployment, scalability, and adaptability to dynamic environments. However, the design and operation of WSNs present numerous challenges that require careful consideration and innovative solutions. One of the primary challenges in WSNs is energy efficiency. SNs typically operate on limited power, and energy conservation is crucial to maximize the network's lifespan. Efficient utilization of energy resources, including techniques such as node sleep scheduling, data aggregation, and energy-aware routing protocols, plays a vital role in prolonging network lifetime and ensuring sustained operation. Another critical aspect is the reliability of data transmission in WSNs. The wireless nature of communication introduces uncertainties such as signal attenuation, interference, and node failures, which can degrade the overall network performance. Robust routing protocols, fault-tolerant mechanisms, and data redundancy techniques are essential to ensure reliable data delivery, even in challenging and dynamic environments. Furthermore, scalability is a significant concern in WSN deployments. As the number of SNs increases, efficient network management, coordination, and data processing become increasingly complex. Scalable protocols and distributed algorithms are necessary to accommodate large-scale deployments, ensuring efficient utilization of network resources and minimizing overhead. Security is another vital aspect of WSNs, as these networks often handle sensitive data. Ensuring confidentiality, integrity, and authentication of transmitted information is crucial to protect against unauthorized access, tampering, and malicious attacks. Robust security mechanisms, including encryption, authentication protocols, and intrusion detection systems, are indispensable in safeguarding the integrity and privacy of WSNs.
In this research paper, the utilization of GWO in WSN research presents an opportunity to improve the efficiency and throughput of these networks. By incorporating the GWO algorithm into the design and optimization process, researchers can explore new possibilities and innovative approaches for overcoming the challenges faced by WSNs. This can lead to improved energy utilization, increased network lifetime, enhanced data transmission reliability, and optimized resource allocation in WSN deployments.
1.1. Motivation and Contribution
The motivation behind utilizing GWO in WSNs stems from the need for efficient resource allocation, improved network lifetime, and enhanced data transmission reliability. Traditional optimization techniques may face limitations when applied to the complex and dynamic nature of WSNs. GWO offers an innovative approach inspired by the social hierarchy and collaborative hunting behavior of grey wolves, which can be harnessed to optimize various aspects of WSNs. By incorporating GWO into WSN research, we aim to explore its unique advantages and contributions to address the existing challenges.
The primary contributions of this research paper are as follows:
• Comparative analysis: We provide a comprehensive comparative analysis of the performance of GWO in WSNs, benchmarking it against other most recent optimization techniques commonly used in WSN research. By conducting extensive experiments and simulations, we aim to evaluate the effectiveness of GWO regarding energy efficiency, network scalability, data transmission reliability, and resource allocation.
• Energy-efficient node placement: We investigate the application of GWO for optimizing node placement in WSNs, considering energy efficiency as a crucial factor. The objective is to determine the optimal locations for SNs to minimize energy consumption while ensuring efficient coverage and connectivity.
• Clustering and routing optimization: We explore the use of GWO for optimizing clustering and routing protocols in WSNs. By leveraging the algorithm's ability to balance exploration and exploitation, we aim to enhance the performance of these protocols for load balancing, data aggregation, and network scalability.
• Adaptability to dynamic environments: We analyze the adaptability of GWO in dynamic WSN scenarios, where nodes may join or leave the network, and the network topology changes over time. We investigate the algorithm's ability to dynamically reconfigure the network, optimize the routing paths, and maintain efficient operation under changing conditions.
• Practical implementation considerations: In addition to theoretical analysis, we consider practical implementation aspects of applying GWO in WSNs. We discuss the computational complexity and communication overhead, ensuring its feasibility for real-world deployments.
The following sections of the paper are structured as follows: In Section 2, a thorough examination of the relevant literature is presented. Section 3 covers the experimental setup and methodology employed to assess the performance of GWO in WSN scenarios. This is followed by Section 4, which provides an in-depth analysis of the results. Lastly, Section 5 concludes the paper by summarizing the contributions made and highlighting potential avenues for future research.
2. Related Work
The recent advancements and deployment challenges associated with node clustering in WSNs were explored in (Younis et al., 2006). In their article, the authors delve into the growing importance of node clustering as a mechanism to enhance the overall performance and energy efficiency of WSNs. The authors discuss various clustering algorithms and protocols, highlighting their strengths and limitations, while also addressing the challenges faced during the deployment of such networks. This comprehensive review serves as a valuable resource for researchers and practitioners seeking to optimize the performance of WSNs through node clustering. A comprehensive study on clustering algorithms for WSNs was conducted in (Abbasi and Younis, 2007). In this research paper, the authors explored the various clustering techniques employed in the context of WSNs. The authors critically analyzed and evaluated different algorithms, considering their advantages, limitations, and suitability for different scenarios. The study aimed to provide researchers and practitioners with a comprehensive understanding of clustering algorithms, enabling them to make informed decisions regarding algorithm selection and implementation in WSNs. An extensive overview of the applications of computational intelligence in WSNs was provided in (Kulkarni et al., 2011). The authors did a systematic review of the various computational intelligence techniques employed in WSNs, including neural networks, evolutionary algorithms, and swarm intelligence, among others. The authors discuss the advantages and limitations of each technique and explore their potential for improving the efficiency and performance of WSNs. This survey is useful for authors and practitioners in the field, offering a comprehensive understanding of the state-of-the-art computational intelligence techniques in WSNs and guiding future research directions. A novel approach called FUCA aimed at enhancing the longevity of WSNs was presented in (Agrawal and Pandey, 2018). The authors propose a clustering technique that assigns unequal roles to SNs based on their RE levels. By employing fuzzy logic principles, FUCA optimizes energy consumption and load balancing, effectively prolonging the network's lifespan. The research contributes to the field of WSNs by offering a practical solution to address energy efficiency concerns in these systems. An adaptive clustering approach for the dynamic routing of WSNs using a generalized ant colony optimization technique was proposed in (Ye and Mohamadian, 2014). In this paper, the authors address the challenges associated with efficient data routing in WSNs. By leveraging the capabilities of ant colony optimization, the proposed approach enables the nodes in the network to dynamically adapt their clustering and routing strategies based on the changing network conditions. The study provides valuable insights into the design and optimization of WSNs, offering potential benefits for various applications in the field. A novel evolutionary-based routing protocol designed specifically for clustered heterogeneous WSNs was presented in (Bara'a and Khalil, 2012). The authors propose an innovative approach that utilizes evolutionary algorithms to optimize the routing process, taking into consideration the diverse characteristics and capabilities of the sensors within the network. In their research, they analyze the effectiveness of the suggested protocol through simulations and compare it with existing routing protocols. The findings indicate that the evolutionary-based protocol demonstrates improved efficiency and effectiveness with regard to energy usage, network lifetime, and data delivery, thus providing valuable insights for the design and optimization of routing protocols in WSNs. A novel energy-aware CH selection approach for WSNs, utilizing Particle Swarm Optimization (PSO) was proposed in (Singh and Lobiyal, 2012). The authors address the crucial challenge of energy consumption in WSNs by devising a mechanism to efficiently select CHs. By employing the PSO technique, they aim to optimize energy utilization and prolong the network's lifespan. This study contributes to the field of WSNs by presenting an innovative method to enhance energy efficiency and ensure the effective functioning of these networks. FLIHSBC, a clustering algorithm for WSNs that aims to prolong the network lifetime was proposed in (Agrawal and Pandey, 2017). The authors’ approach combines fuzzy logic and an improved harmony search technique to efficiently organize SNs into clusters. The study demonstrated the effectiveness of FLIHSBC in enhancing the network lifetime and presented encouraging results for its application in WSNs. A comprehensive survey on the application of PSO in WSNs was conducted in (Kulkarni and Venayagamoorthy, 2011). The authors examined various aspects of PSO implementation, including its advantages, challenges, and future directions. Through a thorough analysis of existing literature, authors contributed to the understanding of PSO's potential in enhancing the performance and efficiency of WSNs. PSO for cluster formation in WSNs was introduced in (S.M. Guru et al., 2005). The authors explore the use of PSO techniques for the formation of clusters in WSNs and present a novel approach that leverages the collective intelligence of particles to optimize the clustering process, improving network efficiency and resource utilization. The proposed protocol contributes to the field of WSNs by proposing an effective method for cluster formation and provides valuable insights into the application of PSO in this context. A study on energy-aware clustering for WSNs using PSO was presented in (Latiff, et al., 2007). The authors investigate the use of PSO techniques to create efficient clustering algorithms that minimize energy consumption in WSNs. The application of PSO and Voronoi diagram techniques for optimizing the coverage of WSNs was explored in (Ab Aziz et al., 2007). The authors investigate the potential of these methods in improving the efficiency and performance of WSNs. The paper provides insights into the integration of PSO and Voronoi diagram algorithms, highlighting their effectiveness in optimizing network coverage, and contributes to the field of intelligent systems and WSNs optimization. A novel approach for selecting the shortest intrapath in a WSN was proposed in (Saravanan and Madheswaran, 2014). By integrating optimization techniques into the weighted minimum spanning tree algorithm, the authors aim to minimize the path length between nodes, thereby minimizing energy consumption and extending network longevity. Their findings offer valuable insights into enhancing the effectiveness of WSNs, contributing to the field of network optimization. A comprehensive study on energy efficient clustering algorithms for WSNs was presented in (Rao and Banka, 2017). The authors propose a novel approach based on chemical reaction optimization to enhance the energy efficiency of clustering algorithms. Through extensive experimentation and analysis, they demonstrate the effectiveness of their proposed approach in achieving significant energy savings in WSNs. This research contributes to the field of WSNs by providing a valuable solution to the energy consumption challenge, which is crucial for extending the network lifetime and improving overall system performance. A novel approach for improving energy efficiency in WSNs by employing a PSO based algorithm for CH selection was proposed in (P. S. Rao et al., 2017). The authors address the crucial problem of energy consumption in sensor networks and present a solution that optimizes the selection of CHs, which play a vital role in data aggregation and communication within the network. Through extensive experimentation and analysis, the authors demonstrate the effectiveness of their proposed algorithm in achieving significant energy savings while maintaining network performance. This research contributes to the field of WSNs and provides valuable insights for designing energy-efficient protocols and algorithms. A novel approach called SGO for achieving energy-efficient clustering in WSNs was presented in (P. Parwekar, 2018). The author focuses on addressing the challenges related to the utilization of energy in WSNs through clustering that optimizes energy utilization and contributes to the field of natural computing research and provides valuable insights into enhancing the energy efficiency of WSNs through the SGO approach. A more advanced version of the GWO algorithm to optimize the routing paths and minimize energy consumption in SNs was proposed in (X. Zhao et al., 2018). Through simulations and performance evaluations, the proposed protocol demonstrates superior energy efficiency with respect to previous methods. This research contributes to the development of more sustainable and efficient WSN solutions, making it a useful tool for researchers and practitioners in the field. A multi-objective Tabu PSO (TS-PSO) approach for the selection of CHs in WSNs was proposed in (Vijayalakshmi and Anandan, 2019). By employing the TS-PSO algorithm, the authors aim to optimize multiple objectives simultaneously, boosting performance of the network as a whole. The research findings demonstrate the effectiveness of the proposed approach in achieving improved CH selection, as evidenced by the significant enhancements in terms of efficiency metrics, such as power usage, network lifespan, and data transfer effectiveness. An enhanced hierarchical clustering approach for mobile WSNs by leveraging type-2 fuzzy logic was introduced in (A. Kousar et al., 2020). The paper contributes to the field of WSNs by proposing an innovative clustering technique that utilizes type-2 fuzzy logic to boost the effectiveness and efficiency of mobile WSNs. The application of a genetic algorithm-based optimization strategy for the selection of CHs in heterogeneous WSNs with single and multiple data sinks was explored in (S. Verma et al., 2019). The study aims to enhance the efficiency and performance of such networks by improving the CH selection process. The authors present their findings and results, highlighting the effectiveness of their proposed approach in improving the overall network performance and contributes valuable insights into optimizing CH selection in WSNs, providing potential benefits for future research and practical implementations in this field. A fuzzy logic-based clustering protocol that aims to enhance energy efficiency within WSNs was proposed in (Rai and Daniel, 2023). The paper investigates the effectiveness of FEEC in reducing energy consumption by optimizing the cluster formation process. The study provides valuable insights and empirical evidence through a thorough evaluation of FEEC's performance. This research contributes to the field of WSNs by offering a promising solution for energy efficiency, which has significant implications for the design and operation of sensor networks. An innovative model for intruder detection utilizing WSNs was developed in (Rai and Daniel, 2022). The authors emphasized energy efficiency as a crucial aspect, aiming to optimize the performance of the system while minimizing power consumption. Their work contributes to the field of intruder detection systems by proposing an effective and energy-efficient solution. The study provides valuable insights for researchers and practitioners interested in enhancing security in WSNs.
3. Experimental setup and methodology
The classic clustering technique called the LEACH protocol plays a significant role in the development of WSNs within a specific region. In this technique, CHs are selected probabilistically, based on a predetermined criterion that considers two parameters: the RE of each CH and the DS from the BS. Once the CHs are determined, the nodes associate themselves with the respective CHs, thereby forming clusters. To optimize this process further, the proposed protocol incorporates gray wolf techniques. These techniques enhance the efficiency and performance of the protocol. Moreover, the network architecture is built in such a way that it facilitates reduced communication distances between the nodes and their respective CHs, as well as between the CHs and the BS. This reduction is achieved through the implementation of a multi-hop routing technique, enabling effective and energy-efficient data transmission throughout the network.
Table 1 shows the coordinates of the network and BS.
Table 1. Details about the WSN region’s parameter
Region Coordinates |
Area measurement in (meters) |
BS coordinates in (meters) |
X |
200 |
100 |
Y |
200 |
100 |
The base station and node distributed around the network’s region is shown in Figure 1 below.
Figure 1. SN distributed around WSN’s region
Algorithm: CH selection
Parameters
SN: SNi
Cluster Radius: CR
CH: CH
Distance between the potential CH and all other nodes in the network: DS
Average distance between the potential CH and the identified nodes: Ads
Begin
1. Initialize the network with a set of SNi.
2. Set the desired number of clusters and the CR
3. Randomly select the first node as a potential CH
4. Calculate the DS
5. Identify the nodes within the CR of the potential CH
6. Calculate the Ads
7. Repeat Steps 4 to 6 for all potential CH
8. Select the potential CH with the minimum Ads as the actual CH
9. Remove the identified nodes from the network.
10. Repeat Steps 3-9 until the desired number of clusters is achieved.
End
3.1. Energy Consumption
Equation 1 and Equation 2 illustrate the energy consumption involved in the transmission and reception of a single packet.
Table 2. Symbols and Specification
Abbreviation |
Name |
CH |
CH |
Ed Reg |
Dissipated Energy for CH selection |
εfs |
Amplifier Energy |
εafr |
Amplifier transmit energy |
R |
Node distance |
Teg |
Transmission Energy |
3.2. Network Architecture
The proposed protocol assumes a homogeneous network with an area measuring 100 x 100 m², where a varying number of nodes between 100 and 400 are randomly deployed. The MATLAB software was utilized to simulate the proposed model. Table 3 displays the parameters chosen for the simulation.
Table 3. Parameter’s Details
Parameters |
Description |
Value |
Eo |
Initial energy of a node |
1J |
ETX |
Data transmission energy |
50 x 10−9 J/bit |
ERX |
Data receiving energy |
50 x 10−9 J/bit |
Efs |
Data transmitting energy by the amplifier when d ≤ d0 |
10 * 10−12 J/bit/m2 |
Earf |
Data transmitting energy by the amplifier when d > d0 |
1.3 × 10−15 J/bit/m4 |
P(i) |
Node’s probability for CH |
0.05 |
Packet Length |
Total length of data to transmit |
6400 bit |
EDA |
Data aggregation energy |
5 x 10−9 J/bit |
rmax |
Maximum round |
500 & 1000 |
3.3. CH Optimization Using the Grey Wolf Algorithm
The GWO algorithm is a nature-inspired optimization algorithm that mimics the hunting behavior of grey wolves. It can be applied to solve various optimization problems, including channel selection in WSNs. In the context of WSNs, channel selection refers to the process of selecting the best set of channels for communication among SNs. The goal is to optimize network performance by minimizing interference, maximizing throughput, and conserving energy.
3.3.1. Explanation of GWO algorithm for channel selection in WSNs
Problem formulation: The first step is to define the problem as an optimization task. In channel selection, this typically involves formulating an objective function that represents the performance metrics to be optimized, such as minimizing interference or maximizing throughput. The decision variables are the channels to be selected for each SN.
Grey Wolf behavior: The GWO algorithm was motivated by the social structure and hunting habits of wild grey wolves. It consists of three types of wolves: alpha, beta, and delta. The alpha wolf is the leader, while the beta and delta wolves are subordinates.
Initialization: The algorithm begins by initializing a population of potential solutions, represented as a set of grey wolves. Each grey wolf corresponds to a potential channel selection configuration.
Hunting behavior: The algorithm iteratively simulates the hunting behavior of grey wolves to search for the best solution. The hunting behavior involves three main steps:
a. Encircling prey: In this step, the alpha wolf searches for the best prey (i.e., the best solution) by exploring the search space. Each grey wolf updates its position based on the position of the alpha wolf.
b. Hunting in packs: The beta and delta wolves follow the alpha wolf and update their positions accordingly. They search around the position of the alpha wolf to improve the exploration capability.
c. Prey location: At each iteration, the grey wolves update their positions based on the positions of the alpha, beta, and delta wolves. This update is performed using mathematical equations inspired by the hunting behavior of wolves.
Solution evaluation: After updating the positions, the objective function is evaluated for each grey wolf, representing the performance of the corresponding channel selection configuration.
Dominance and selection: The next step involves comparing the performance of the current solutions and identifying dominant solutions. Dominant solutions are those that provide better performance in terms of the objective function. Non-dominant solutions are discarded.
Reproduction: The dominant solutions are selected as parents for reproduction. The offspring are generated through crossover and mutation operators, which create new channel selection configurations.
Replacement: The offspring generated in the previous step replace the weakest members of the population. This ensures that the population evolves towards better solutions over time.
Termination condition: The algorithm iterates through the hunting behavior steps until a termination condition is met. This condition can be a maximum number of iterations, a predefined level of performance improvement, or other criteria specific to the problem being solved.
Final solution: The algorithm returns the best channel selection configuration found during the iterations, which represents the optimal solution according to the defined objective function.
3.4. Proposed Protocol
Algorithm: PSO
Initialize parameters
CH: CH
Initial population: Pi
Fitness Value of Grey wolf: Fg
Population size: Ps
Maximum iterations: Mi
Search space boundaries: Sb
Convergence parameters
The tolerance values: Tv
Maximum generations without improvement: Mg
Begin
1. Generate a Pi of grey wolves
2. Each grey wolf represents a potential CH.
3. The Ps should be set according to the problem's complexity and desired convergence speed.
4. Evaluate the Fg each grey wolf by applying the objective function to measure the quality of the corresponding CH.
5. The fitness function should consider the problem-specific criteria, such as energy efficiency, coverage, connectivity, or other performance metrics.
6. Identify the three types of grey wolves: alpha (the best), beta (the second best), and delta (the third best) based on their fitness values. Update the positions of these grey wolves.
7. Update the positions of the remaining grey wolves using the following formula:
X_new = X_alpha - A * D_alpha
where
X_new is the new position
X_alpha is the position of the alpha grey wolf
A is a random coefficient between 0 and 2
D_alpha is the distance between the current grey wolf and the alpha grey wolf.
8. Apply the boundary conditions to the positions of all grey wolves to ensure they remain within the feasible search space.
9. Evaluate the Fg of the updated grey wolves.
10. Compare the updated Fg with the previous ones.
11. If
12. The fitness has improved, update the positions and Fg accordingly.
13. Else
14. Remain same position
15. End
16. Check the convergence criteria.
17. If
18. The termination condition is met
19. Stop the algorithm and return the best solution found so far.
20. Else
21. Go to the next iteration.
22. End
23. Repeat steps 6- until the convergence criteria are satisfied.
24. Output the best CH obtained by the GWO algorithm.
End
The figure labeled as Figure 2 provides a visual representation of the GWO algorithm in the form of a flow chart.
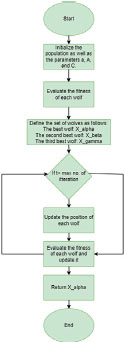
Figure 2. Flow chart of GWO
3.5. Result and Discussion
In the comparative analysis section, a comparison has been made of three different methods: Energy Efficient GWO Protocol (EE-GWOP), LEACH (Low Energy Adaptive Clustering Hierarchy), and SEP (Slotted Energy Protocol). The purpose of this analysis is to evaluate and compare these methods based on certain criteria or performance metrics. Figure 3 illustrates the comparative analysis in terms of the first dead node. This figure likely presents a graphical representation or chart that shows the occurrence of the first dead node for each method.
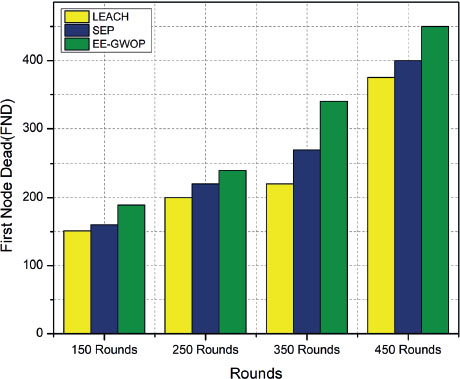
Figure 3. First Node Dead in the network
It helps to understand which method experiences the failure of the first node earliest or how the three methods compare in terms of early node death. Figure 4, on the other hand, depicts the comparative analysis in terms of the half node dead, and Figure 5 depicts the comparative analysis in terms of the last node dead. It is also a graphical representation or chart that showcases the lifespan or survival time of the nodes in each method. This figure provides insights into when the last node fails or becomes inactive for each method and enables a comparison between them.

Figure 4. Half Node Dead in the network
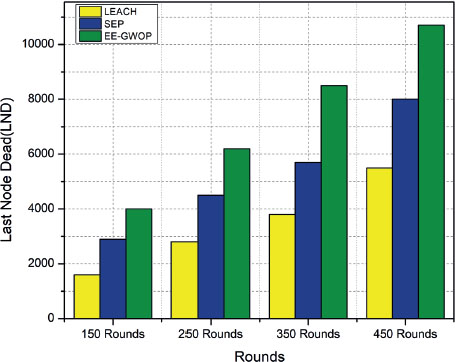
Figure 5. Last Node Dead in the network
This comparison helps in understanding the relative strengths and weaknesses of each method and facilitates decision-making or further analysis. To fully comprehend the findings and implications of these figures and table, it would be necessary to refer to the accompanying text or research paper where this information is published.
The details and specific results mentioned in the text can provide a more comprehensive understanding of the conducted comparative analysis.
Table 4 represents the comparative analysis for the proposed model. It is a tabular presentation that likely includes various performance metrics or evaluation criteria. The table allows for a direct comparison between the three methods, providing a summary of their performance in terms of the specific metrics being considered.
Table 4. Dead Node Analysis
|
First Node Dead |
Half Node Dead |
Last Node Dead |
|||||||||
|
100 Nodes |
200 Nodes |
300 Nodes |
500 Nodes |
100 Nodes |
200 Nodes |
300 Nodes |
500 Nodes |
100 Nodes |
200 Nodes |
300 Nodes |
500 Nodes |
EE-GWOP |
190 |
238 |
342 |
328 |
2000 |
4000 |
6400 |
7000 |
3998 |
6198 |
8499 |
10698 |
SEP |
159 |
219 |
269 |
268 |
1400 |
2500 |
3700 |
5500 |
2910 |
4499 |
5695 |
7994 |
LEACH |
148 |
198 |
218 |
224 |
900 |
1800 |
2700 |
3900 |
1598 |
2797 |
3798 |
5496 |
3.5.1. Evaluation of the Proposed Model Using Packet-to-Base Station Analysis
This section focuses on evaluating the proposed model by analyzing packet transmission to the base station (BS). To compare the performance of the proposed model (EE-GWOP) with other existing models (LEACH and SEP), simulations were conducted for 600, 800, and 1000 rounds. The results of this comparative analysis are summarized in Table 5, which provides insights into the performance of the proposed model relative to LEACH and SEP.
Table 5. Number of packets sent.
Rounds |
EE-GWOP-150 |
SEP-150 |
LEACH-150 |
EE-GWOP-250 |
SEP-250 |
LEACH-250 |
EE-GWOP-450 |
SEP-450 |
LEACH-450 |
600 |
105 |
82 |
67 |
185 |
168 |
146 |
384 |
333 |
310 |
800 |
110 |
90 |
78 |
197 |
177 |
148 |
378 |
358 |
325 |
1000 |
118 |
92 |
76 |
199 |
178 |
150 |
382 |
347 |
325 |
Figures 6, 7, 8 and the Table 5 provides the performance results for three different protocols, namely EE-GWOP, SEP, and LEACH, at different rounds (measured in hundreds). The performance metric shown in the table is represented by numerical values for each protocol at specific rounds. At round 600, the performance values for EE-GWOP-150, SEP-150, and LEACH-150 are 105, 82, and 67, respectively. Similarly, at round 800, the performance values are 110, 90, and 78 for EE-GWOP-150, SEP-150, and LEACH-150, respectively. Moving on to round 1000, the performance values for EE-GWOP-150, SEP-150, and LEACH-150 are 118, 92, and 76, respectively. It is important to note that the values for EE-GWOP-150 represent the performance of the EE-GWOP protocol with a specific parameter setting (e.g., 150). The same pattern of performance values is repeated for the other two sets of protocols (EE-GWOP-250, SEP-250, LEACH-250, EE-GWOP-450, SEP-450, LEACH-450). The values for each protocol at each round represent their respective performance in the given scenario.

Figure 6. Packets sent per second for 150 nodes
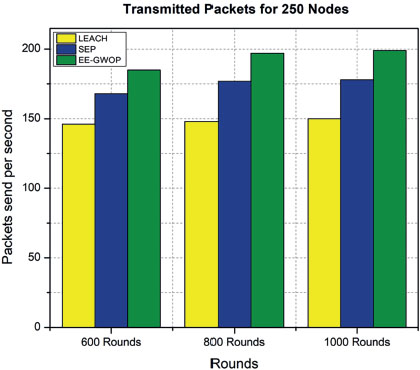
Figure 7. Packets sent per second for 200 nodes
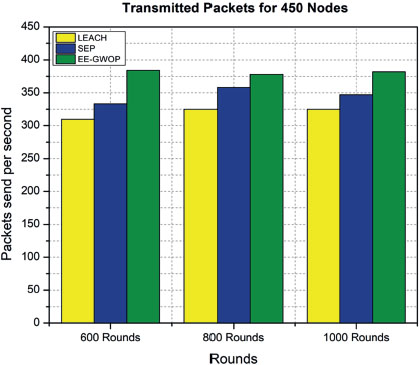
Figure 8. Packets sent per second for 450 nodes
3.5.2. Evaluation of the Proposed Model Using Residual Energy
In this section, the proposed model is demonstrated based on the reliability evaluation RE of the network. The goal is to assess the reliability of the network using the proposed model compared to two other methods, EE-GWOP, LEACH, and SEP. Figure 10 displays the RE at 1000 rounds for networks with different numbers of nodes: 150, 250, 350, and 450. The figure presents a graphical representation or chart that shows the RE achieved by the proposed model, EE-GWOP, LEACH, and SEP at each round. This comparison helps in understanding how the proposed model performs in terms of network reliability compared to the other two methods across different numbers of nodes. Table 6 presents the comparative analysis of the proposed model. It is a tabular presentation that includes the reliability evaluation results for the proposed model, EE-GWOP, LEACH, and SEP. The table allows for a direct comparison of the performance of these methods in terms of reliability. It may include quantitative measures or metrics, such as RE percentages, to provide a summary of the comparative analysis.
Table 6. RE
|
RE |
|||
Nodes Round (1000) |
150 Nodes |
250 Nodes |
350 Nodes |
450 Nodes |
EE-GWOP |
65 |
70 |
74 |
74 |
SEP |
55 |
60 |
64 |
63 |
LEACH |
40 |
50 |
55 |
57 |
To fully grasp the findings and implications of Figure 9 and Table 6, it would be important to refer to the accompanying text or research paper where this information is published. The detailed explanation and specific results mentioned in the text can provide a more comprehensive understanding of the conducted comparative analysis and the reliability of the proposed model.
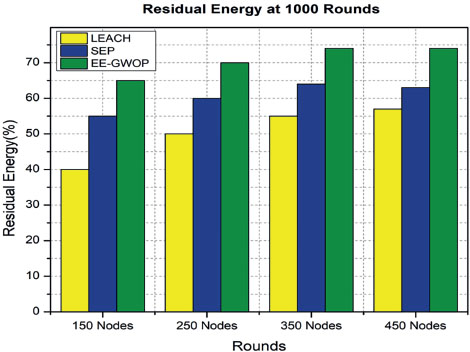
Figure 9. RE of nodes
To fully grasp the findings and implications of Figure 10, Table 7 shows the average RE for different numbers of nodes at various rounds (measured in thousands). Three different protocols, namely EE-GWOP, SEP, and LEACH, are compared based on their average RE values. At round 500, EE-GWOP has an average RE of 4.7, while SEP and LEACH have values of 4.0 and 3.6, respectively. As the rounds progress, the average RE decreases for all protocols, indicating the depletion of energy in the network due to node operations. By round 1000, EE-GWOP shows a lower average RE of 4.0 compared to SEP and LEACH, which have values of 3.6 and 3.0, respectively. This trend continues as the rounds increase. At round 2500, the average RE for EE-GWOP decreases to 2.5, while SEP drops to 1.5, and LEACH decreases to 1.0. This suggests that EE-GWOP protocol manages energy more efficiently compared to the other two protocols, resulting in a higher RE level at this stage. As the rounds progress further, EE-GWOP continues to outperform SEP and LEACH. At round 3000, EE-GWOP has an average RE of 1.5, while SEP has 0.8. LEACH, on the other hand, reaches 0, indicating that all nodes in the LEACH protocol have exhausted their energy by this point. Finally, at round 3500, EE-GWOP maintains a small average RE of 0.5, indicating a minimal amount of energy remaining. SEP and LEACH, however, have completely depleted their energy at this stage, with average RE values of 0. Overall, the table demonstrates that the EE-GWOP protocol consistently maintains higher average RE levels compared to SEP and LEACH, showcasing its energy efficiency and improved longevity of the network before energy depletion.
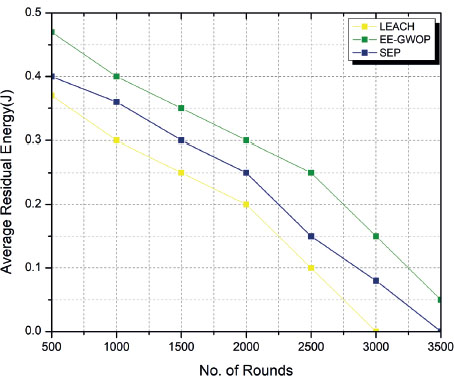
Figure 10. Average energy of nodes
Table 7: Average RE
|
Average RE |
||
Nodes Round (1000) |
EE-GWOP |
SEP |
LEACH |
500 |
4.7 |
4.0 |
3.6 |
1000 |
4.0 |
3.6 |
3.0 |
1500 |
3.5 |
3.0 |
2.5 |
2000 |
3.0 |
2.5 |
2.0 |
2500 |
2.5 |
1.5 |
1.0 |
3000 |
1.5 |
0.8 |
0 |
3500 |
0.5 |
0 |
0 |
4. Conclusion and Future Scope
The proposed research introduces a model called EE-GWOP, which focuses on selecting CH based on probability and optimizes it using GWO. The hybrid approach of GWO and LEACH protocols is employed to determine the fittest node, considering the node's RE and DS. The selected fittest node participates in the CH selection process. For simulation purposes, a 100 x 100 m² region of interest is utilized, accommodating varying numbers of nodes. The proposed model is evaluated for each node count, and a comparative analysis is conducted with LEACH and SEP protocols. The results demonstrate that the proposed model outperforms the other protocols in multiple performance parameters. In terms of the number of dead nodes per round, the EE-GWOP model exhibits superior performance. Furthermore, EE-GWOP achieves higher packet transmission rates to the BS compared to SEP and LEACH protocols. Additionally, EE-GWOP maintains relatively higher RE levels, measured in joules. It is important to note that the experiments conducted in this research were limited to a static and homogeneous network. Future experiments aim to expand the study to include heterogeneous and dynamic networks. Additionally, energy-efficient networks will be explored for intrusion detection and to ensure proper coverage and connectivity in the target area of the WSN.
5. Conflict of Interest
Authors declare that they have no conflict of interest.
6. References
Ab Aziz, N. A. B., Mohemmed, A. W., & Sagar, B. D., 2007. Particle swarm optimization and Voronoi diagram for wireless sensor networks coverage optimization. In Intelligent and Advanced Systems, 2007. ICIAS 2007. International Conference (pp. 961–965). IEEE. https://doi.org/10.1109/ICIAS.2007.4658528
Abbasi, A. A., & Younis, M., 2007. A survey on clustering algorithms for wireless sensor networks. Computer communications, 30(14-15), 2826–2841. https://doi.org/10.1016/j.comcom.2007.05.024
Agrawal, D., & Pandey, S., 2017. FLIHSBC: fuzzy logic and improved harmony search based clustering algorithm for wireless sensor networks to prolong the network lifetime. In International Conference on Ubiquitous Computing and Ambient Intelligence (pp. 570–578). Springer, Cham. https://doi.org/10.1007/978-3-319-67585-5_56
Agrawal, D., & Pandey, S., 2018. FUCA: fuzzy-based unequal clustering algorithm to prolong the lifetime of wireless sensor networks. International Journal of Communication Systems, 31(2), e3448. https://doi.org/10.1002/dac.3448
Bara'a, A. A., & Khalil, E. A., 2012. A new evolutionary based routing protocol for clustered heterogeneous wireless sensor networks. Applied Soft Computing, 12(7), 1950–1957. https://doi.org/10.1016/j.asoc.2011.04.007
Guru, S. M., Halgamuge, S. K., & Fernando, S., 2005. Particle swarm optimisers for cluster formation in wireless sensor networks. In Intelligent Sensors, Sensor Networks and Information Processing Conference. Proceedings of the 2005 International Conference (pp. 319–324). IEEE. https://doi.org/10.1109/ISSNIP.2005.1595599
Kousar, A., Mittal, N., & Singh, P., 2020. An improved hierarchical clustering method for mobile wireless sensor network using type-2 fuzzy logic. In Proceedings of ICETIT 2019 (pp. 128–140). Springer, Cham. https://doi.org/10.1007/978-3-030-30577-2_11
Kulkarni, R. V., Forster, A., & Venayagamoorthy, G. K., 2011. Computational intelligence in wireless sensor networks: A survey. IEEE communications surveys & tutorials, 13(1), 68–96. https://doi.org/10.1109/SURV.2011.040310.00002
Kulkarni, R. V., & Venayagamoorthy, G. K., 2011. Particle swarm optimization in wireless-sensor networks: A brief survey. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 41(2), 262–267. https://doi.org/10.1109/TSMCC.2010.2054080
Latiff, N. A., Tsimenidis, C. C., & Sharif, B. S., 2007. Energy-aware clustering for wireless sensor networks using particle swarm optimization. In Personal, Indoor and Mobile Radio Communications, 2007. PIMRC 2007. IEEE 18th International Symposium (pp. 1–5). IEEE. https://doi.org/10.1109/PIMRC.2007.4394521
Parwekar, P., 2018. SGO a new approach for energy efficient clustering in WSN. International Journal of Natural Computing Research (IJNCR), 7(3), 54–72. https://doi.org/10.4018/IJNCR.2018070104
Rai, A. K. and Daniel, A. K., 2023. FEEC: fuzzy based energy efficient clustering protocol for WSN. International Journal of Systems Assurance Engineering and Management, 14, 297–307. https://doi.org/10.1007/s13198-022-01796-x
Rai, A. K., & Daniel, A. K., 2022. Energy-Efficient Model for Intruder Detection Using Wireless Sensor Network. Journal of Interconnection Networks, 22, 1–22. https://doi.org/10.1142/S0219265921490025
Rao, P. S., & Banka, H., 2017. Energy efficient clustering algorithms for wireless sensor networks: novel chemical reaction optimization approach. Wireless Networks, 23(2), 433–452. https://doi.org/10.1007/s11276-015-1156-0
Rao, P. S., Jana, P. K., & Banka, H., 2017. A particle swarm optimization-based energy efficient cluster head selection algorithm for wireless sensor networks. Wireless Networks, 23(7), 2005–2020. https://doi.org/10.1007/s11276-016-1270-7
Saravanan, M., & Madheswaran, M., 2014. A hybrid optimized weighted minimum spanning tree for the shortest intrapath selection in wireless sensor network. Mathematical Problems in Engineering. https://doi.org/10.1155/2014/713427
Singh, B., & Lobiyal, D. K., 2012. A novel energy-aware cluster head selection based on particle swarm optimization for wireless sensor networks. Human-Centric Computing and Information Sciences, 2(1), 13. https://doi.org/10.1186/2192-1962-2-13
Verma, S., Sood, N., & Sharma, A. K., 2019. Genetic algorithm-based optimized cluster head selection for single and multiple data sinks in heterogeneous wireless sensor network. Applied Soft Computing, 85, 105788. https://doi.org/10.1016/j.asoc.2019.105788
Vijayalakshmi, K., & Anandan, P., 2019. A multi-objective Tabu particle swarm optimization for effective cluster head selection in WSN. Cluster Computing, 22(5), 12275–12282. https://doi.org/10.1007/s10586-017-1608-7
Ye, Z., & Mohamadian, H., 2014. Adaptive clustering based dynamic routing of wireless sensor networks via generalized ant colony optimization. Ieri Procedia, 10, 2–10. https://doi.org/10.1016/j.ieri.2014.09.063
Younis, O., Krunz, M., & Ramasubramanian, S., 2006. Node clustering in wireless sensor networks: recent developments and deployment challenges. IEEE network, 20(3), 20–25. https://doi.org/10.1109/MNET.2006.1637928
Zhao, X., Zhu, H., Aleksic, S., & Gao, Q., 2018. Energy-efficient routing protocol for wireless sensor networks based on improved grey wolf optimizer. KSII Transactions on Internet & Information Systems, 12(6), 4. https://doi.org/10.3837/tiis.2018.06.011