
Regular Issue, Vol. 10 N. 4 (2021), 321-337
eISSN: 2255-2863
DOI: https://doi.org/10.14201/ADCAIJ2021104321337
 |
ADCAIJ: Advances in Distributed Computing and Artificial Intelligence Journal
Regular Issue, Vol. 10 N. 4 (2021), 321-337 eISSN: 2255-2863 DOI: https://doi.org/10.14201/ADCAIJ2021104321337 |
Taking Drones to Next Level: The Performance Evaluation of MAA with BCO Routing Protocols for Flying Ad-hoc Networks (FANETs)
Altaf Hussain*a,b, Habib Ullah Khana, Shah Nazirc, Tariq Hussainb,d and Ijaz Ullahe
a Department of Accounting and Information Systems, College of Business and Economics, Qatar University, Doha, Qatar
b Institute of Computer Sciences and IT (ICS/IT), The University of Agriculture Peshawar Pakistan
c Department of Computer Science, University of Swabi, Swabi Pakistan
d School of Computer Science and Information Engineering, Zhejiang Gongshang University Hangzhou, China
e University of Rennes 1, France
altafkfm74@gmail.com, habib.khan@qu.edu.qa, shahnazir@uoswabi.edu.pk, uom.tariq@gmail.com, ijaz_flair@yahoo.com
*Correspondence Email: altafkfm74@gmail.com
ABSTRACT
Flying Ad-hoc Network (FANET) is a special member/class of Mobile Ad-hoc Network (MANET) in which the movable nodes are known as by the name of Unmanned Aerial Vehicles (UAVs) that are operated from a long remote distance in which there is no human personnel involved. It is an ad-hoc network in which the UAVs can more in 3-D ways simultaneously in the air without any onboard pilot. In other words, this is a pilot-free ad-hoc network also known as Unmanned Aerial System (UAS) and the component introduced for such a system is known as UAV. There are many single UAV applications but using multiple UAVs system cooperating can be helpful in many ways in the field of wireless communication. Deployments of these small UAVs are quick and flexible which overcome the limitation of traditional ad hoc networks. FANETs differ from other kinds of ad-hoc networks and are envisioned to play an important role where infrastructure operations are not available and assigned tasks are too dull, dirty, or dangerous for humans. Moreover, setting up to bolster the range and performance of small UAV in ad-hoc network lead to emergent evolution with its high stability, quick deployment, and ease-of-use for the formation of the network. Routing and task allocation are the challenging research areas of the network with ad hoc nodes. The paper overview is based on the study of biological-inspired routing protocols Moth-and-Ant (MAA) and Bee Colony Optimization (BCO) routing protocol with performance evaluation. The proposed evaluation’s simulations were conducted by performance parameters Packet Delivery Ratio, End to End Delay, Transmission Loss and Network Lifetime.
KEYWORDS
FANET; Routing Protocols; BCO; UAV; MAA inspired Routing; Packet Delivery Ratio; End to End Delay; Transmission loss; Network Lifetime.
1. Introduction
Unmanned Aerial Vehicles (UAVs) are designed to operate in long endurance despite harsh weather conditions and can resist wind gusts. In its high Detection, Recognition, and Identification (DRI) capabilities and resistance to jamming and interference, it is ideally suited for site protection and civil security. The nature of the FANET is their fast-changing topology, frequently network partitioning (nodes leave or join), and its movement in 2 or 3 Dimensions. It has self-organizing, self-healing abilities that increase the life of wireless networks. Protocols on the other hand can run in different layers to handle dynamic entering and leaving of nodes. Each flying UAV in FANET considers as a router to achieve real-time effective communication with advanced features of perfect actuators, the latest software, and best loop principles. FANET is a subclass of VANET (Vehicular Ad-hoc Network) that governs the autonomous movement of UAV and application scenarios that take place in FANETs are search and rescue operations, forest fire detection, traffic and urban monitoring, reconnaissance, and patrolling, agricultural management, environmental sensing, and relaying network (Alshbatat & Dong, 2010). The multi-UAV plays an important role in choosing a networking architecture for best performance. There exist different networking architectures proposed and emerged. The basic one is the centralized link communication between UAVs and a single ground station in a fixed topology in which a ground station is responsible for creating the communication between these UAVs as well as coordinating their movements. The usage of a Ground Control Station (GCS) might result in traffic congestion that accordingly influences system functionality (Bekmezci et al., 2013). QoS (Quality of Service) in the FANET is very important in the case of emergency services. Data packet delivery ratio and delay are also important factors for such a case. Figure 1 shows applications of FANET that could increase the rescuing chances in natural disaster environments and many more. FANET provides real-time quick disaster monitoring with a temporary wireless communication setup and provides public safety services to interested parties as well as in remote sensing, traffic monitoring, managing wildfire, relaying network, and border surveillance.
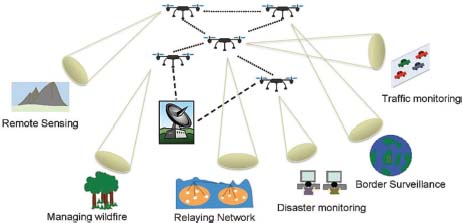
Figure 1: Application scenario of FANET (Bekmezci et al., 2013).
An unpredictable event like wildfires occurs in timberland areas (forests and prairies) etc. but could happen in urban areas (buildings and homes) etc. Three possible network architectures proposed for the multi-UAV system are satellite, cellular, and ad hoc each of which solves or alleviates the problems in the direct link approach (Karaboga, 2005). Networking architecture for FANET established the wireless ad hoc network among UAVs which could work as a relay node. These relay nodes work together to forward the data until it reaches the destination. There are two segments involves according to the communication type. The first one is called “ground or satellite segment” in which some of UAV can directly communicate with ground station or via satellite in UAV-to-infrastructure communication type while the other called the “aero segment” in which the UAV does not have any direct links with the ground station and can connect. This communication type is known as UAV-to-UAV communication. It is important to emphasize that changing the orientation from using one UAV to using several small UAVs needs to develop new networking technologies among UAVs. FANET is within that context considered as a popular technology for communication networking among multi UAVs for extending the operational ambit and ranging but also capable of providing quick and reliable response time (Bekmezci et al., 2015). The contribution of the Research is fowling.
The main contribution of the research is the performance evaluation of biological-inspired FANETs routing protocols such as moth-and-ant (MAA) and bee ad-hoc routing protocols. The performance of routing protocols is different perspective features and limitations. Also, these protocols are evaluated with ad-hoc traditional routing proctors i.e., DSR (Dynamic Source Routing), AODV (Ad-hoc On-demand Distance Vector) and DSDV (Destination Sequence Distance Vector), etc. when the number of nodes increased in the network, what will be the impact on throughput and movable nature topology. Each protocol has the same fractures which perform a specific function in the network. If one protocol is adaptable for the dynamic topology to keep countenance communication, then the other one is responsible for throughput in the network, when the network size and node are increased. The MAA and bee ad-hoc protocol gives better performance in geographical scalability. Give high throughput as compared to DSR, AODV, and DSDV.
The rest of the paper is organized as, in section 2, the literature review of the Moth-and-Ant (MAA) with Bee Ad-hoc Routing Protocols are given also known as state-of-the-art. Similarly, classifications of FANET routing protocols are explained. Section 3 explains the biologically inspired algorithms and section 4 explains the performance evaluation of MAA and Bee Ad-hoc routing protocols. Finally, section 5 conclusion and future work are suggested, and it concludes the paper.
2. Related Work
Routing and handling the resources efficiently among the nodes with cooperative behavior are the key tasks in the field of ad hoc mode like FANET. Routing and task allocation can be achieved by picking examples from the natural world. Based on the social behavior of biologically inspired in the field of wildlife, researchers have modified the traditional protocols and algorithms to enhance the network lifetime and stability period to achieve reliable communication and reduce end-to-end delay and path-loss. The selection of protocol for routing and algorithm for cooperative task allocation is a complex task in FANETs and depends on the application requirements. All these are depending on total users and their mobility level.
The algorithms for routing are used for packet data delivery and are applied to find the best route through the secure and shortest route for data sending from the source to the destination. Selection criteria for optimal routes also known as metrics may include information such as the route length (steps number), reliability, delay, bandwidth, load, communication cost, power consumption, etc. Swarm Intelligence (SI) so-called swarm algorithm is used when external management, coordination, and control are not available to solve the complex dynamic problems of collaborative work. Bio-inspired protocols AntHocNet, Bee-Ad-Hoc, and moth-ant inspired routing is efficient in comparison with the traditional routing protocols. On the other hand, the algorithm for distribution of different tasks among nodes to utilize the available nodes efficiently, HMADSO (Hill Myna and Desert Sparrow Optimization) Algorithm is discussed (Billington & Yuan, 2009). The concept of algorithm based on biologically inspired in nature is used successfully for problem solution of complex optimization in FANET. Nature-inspired behavior was analyzed by authors in (Bujari et al., 2017), and presented the biological concept of the honeybee in which bees of the hive divided into three main groups: i) Employed bees ii) Onlookers iii) Scouts. Authors (Cheng et al., 2007) implemented a bee algorithm for MANETs for peer-to-peer file searching and explore the bee behavior. Scouting is the first stage which can be further divided into two scouting stages the first one is forward scouting and the second stage is backward scouting. The role of the forward scouts is to scrutinize the network for the destination node. Information is carried by a forward scout that consists of four categories: Scout ID; Source node ID; Minimal residual energy; and Number of hops.
A moth-inspired routing protocol was proposed in (Pham et al., 2006) for mobile networks to improve communication performance. This protocol may reduce packet loss and improve the throughput under certain conditions. Further, it has the choice to know the non-optimal routing path and analyze to reduce the delay and communication overhead in the network. Some routing protocols of other kinds of ad hoc networks have been modified for application in new ad hoc families like FANET. These routing protocols are classified into six different categories (Dhurandher et al., 2011). FANETs are high-speed data transfer, high nodes mobility, and hence not easy to find the universal problem solution of routing and task allocation in FANET. Categorizations of routing protocols for FANETs are described as follows.
2.1. Classification of FANET’s routing protocols
Categorization of routing protocols and applicability of the protocols in FANET are described as follows 1) Static routing protocols 2) Proactive routing protocols 3) Reactive routing protocols 4) Hybrid routing protocols 5) Geographic/ 3-D routing protocols 6) Hierarchical routing protocols.
• Static Routing Protocols: The static type of protocols holds the static tables these tables are computed and laden once at the starting of time operation. These tables cannot be updated during task operations. Static protocols are not scalable and cannot handle the fast-dynamic topology changes in FANET but are useful in academic interest.
• Data-Centric: Data-centric routing presented in (Ahmed, 2020) depended on the content of data and can be used for one to many communication models. This is best for cluster topologies where broadcasting can be done by Cluster Head (CH) to other nodes in the cluster. CHs are responsible to extend the reliable communication distance.
• Multi-Level Hierarchical Routing (MLHR): Based on cluster topology MLHR proposed in (Flury & Wattenhofer, 2008) and solved the large-scale scalability problems in vehicular networks. In FANET multiple UAVs can be grouped to form clusters in which CH (Cluster Head) can link outside the cluster. CH is responsible to disseminate data to another UAV in clusters. In FANET speedy change of CH enforce large overhead in the network.
• Load Carry and Deliver (LCAD): LCAD proposed in (Forsmann et al., 2007) in which node at the ground is responsible to pass the required information to UAV which securely carries it to destination. LCAD has higher throughput but data delivery delay is longer due to the use of a single UAV. Its objective is to maximize throughput and ensure security.
2.2. Proactive Routing Protocols
Proactive Routing Protocols (PRPs) contain a table in their nodes. These protocols store the route information of other nodes within the network. In PRPs, nodes maintain their table up to date and contain only the latest data of the routes. Data is transmitted by sharing control messages (HELLO, TC) in it, and the routing procedure is performed by each node without any direction from others. It is important in FANET to maintain the tables up to date at the time of topology changes. On the other hand, overhead and large bandwidths are the main limitations in it.
• Optimized Link State Routing (OLSR): OLSR is the most adaptive routing algorithm proposed in (Frew & Brown, 2009) for ad hoc networks. Routes are set at startup in it for all destinations and then by property of proactive routing, nodes within the network contain the updated data of the routes. These nodes are responsible to share the topology information regularly with other nodes by broadcasting the link-state costs of their adjacent nodes using a flooding strategy.
• Directional-Optimized Link State Routing (D-OLSR): D-OLSR is an extension of OLSR and was proposed by authors in (Haas, 1998). It is differing from OLSR in the selection of multipoint relays. A node within the network measures the distance to the destination from the routing table and when found the distance is long to the destination it will go on a directional antenna through D-OLSR and when the distance to the destination is found smaller than it will go back to OLSR and performs Omi directional antenna. D-OLSR has less end-to-end delay than OSLR.
• Multipath Optimized Link State Routing (MP-OLSR): The algorithm MP-OLSR is based on OLSR and is proposed in (Jacquet et al., 2001) to improve the efficiency of data transmission using multipath.MP-OLSR is an application layer protocol. This protocol obtains extensibility by employing different link metrics and cost functions with flexibility.
• Destination Sequence Distance Vector (DSDV): Authors in (Kaddoura et al., 2011) proposed DSDV that used the sequence numbers to avoid the loops and to trace the best route. Based on the Bellman-Ford algorithm, DSDV is proposed and uses with minor adjustment of ad hoc networks. At the time of topology changes the incremental dump packets are sent only. Although DSDV slightly reduces the network overhead large overhead is there because of periodic updates and required large bandwidth for the update process which is necessary for topology changes.
• Fisheye State Routing (FSR): FSR is the class of PRP and the authors proposed it in (Karp & Kung, 2000). FSR reduces the overhead by mean of more frequent small table update to the adjacent nodes. The idea for such a case is known as fisheye scope. One of the main disadvantages of this routing is the inaccuracy of the network where nodes are high mobility and dynamic topology. Similarly, based on PRP, Border Gateway Protocol with Mobile Extension (BGP-MX) enables inter-domain communication in the Air Born networks scenario. It allows a high mobility network to stay connected (Kim & Lee, 2017). A proactive routing protocol based on the ADS-B setup for aeronautical ad hoc networks is proposed in (Ko & Vaidya, 2000). It is a topology-aware protocol, and the aim of this protocol is to get rid of the traditional routing beaconing and presented the velocity base metric for next-hop selection.
2.3. Reactive Routing Protocols
Reactive Routing Protocols (RRPs) are commonly known as on-demand routing protocols and are designed to overcome the limitations of overhead in proactive routing protocols. RRP a route is stored in nodes when they communicate with each other. Further, the nature of on-demand assures no periodic messaging for connectivity. Due to this property RRPs are bandwidth efficient. The process of tracing routes can consume a long time and caused high latency. There are two types of RRPs namely source routing and hop by hop routing. In source routing, the data packet contains the source to destination address completely and based on this information intermediate nodes can forward packets only. Secondly, hop by hop routing, data packet contains a destination address and next-hop address. In this case, intermediate nodes only maintain a routing table to forward data.
• Dynamic Source Routing (DSR): Dynamic Source Routing (Kuperman et al., 2014) in RRP is usually designed to use in multi-hop ad hoc networks. It permits networks to be self-healing, self-organizing without any requirement of existing infrastructure. DSR is on-demand routing and scales automatically. The mechanism of route discovery and route maintenance in DSR makes it capable to discover and maintain routes to the destination. It has the advantage to allow choice from many routes to any destination like load balancing.
• Ad hoc On-Demand Distance Vector (AODV): The authors proposed AODV in (Leonov, 2016). It is an RRP using hop by hop phenomena and can easily adjust in high mobility and dynamic change scenarios. It has low overheads, processing, and low network utilization. It can specify unicast routes to a destination within the network. Next hop information in the network corresponding to each data transmission contains by source and relay nodes. These data packets have an only destination IP address which overcomes the overhead. To extending the standard routing algorithm of Open Shortest Path First which is widely used in a wired network the extension MANET Designated Routers (OSPF-MDR) is presented for effectively used in wireless (Lidowski et al., 2009). Dynamic MANET On-demand (DYMO) routing protocol is presented in (Liu & Wu, 2009) and the aim of this routing protocol is effective for route discovery and route maintenance.
2.4. Hybrid Routing Protocols
Hybrid Routing Protocols (HRPs) overcomes limitations faced in PRPs and RRPs i.e. reduce the overhead caused by control messages and decrease the large latency that comes from the initial route discovery process respectively. These routing protocols types are suitable for a large network. In HRP, the network is divided into two different routing zones known as intra zone routing and inters zone routing. Proactive routing can be performed by using intra zone routing while reactive routing approach using inter-zone. Hybrid routing sets the scheme according to the network properties and is effective for MANETs. However, nodes’ behaviors in FANET make it complicated to maintain the information accordingly. It is hard to implement in dynamic networks.
2.5. Geographic 2-D and 3-D Protocols
Geographic schemes are considered the geographic positions of nodes and known information about nodes. The source in the geographic model knows the geographical place of the node and messages are sent to the destination without route discovery. Many routing strategies for 2-dimensional networks have been developed by adapting planar geometry. The main technique use for this model is greedy forwarding. The main purpose is to minimize the number of hops and contain only local information. In this way, every node forwards the message to the node adjacent to the destination. In the FANET application, it may be more convenient by using 3 dimensions. High mobility and dynamic topology changes need 3-D environments to scale the parameters.
2.6. Hierarchical Protocols
Hierarchical protocols are the set of routing solutions. These protocols are proposed for problem solutions of scalability and overheads. Hierarchical protocols are one of the possible routing solutions in FANET (Figure 2). Different hierarchy of protocols reduces network congestion. The hierarchical protocols divided the plan into different levels and routing is performed in these levels. The concept of Cluster develops for different target operation areas. Each cluster in the selected region has a principal cluster called CH and each node in the clusters are within the range of CH for reliable transmission. CH provides links outside the region with other networks for large-scale transmission.
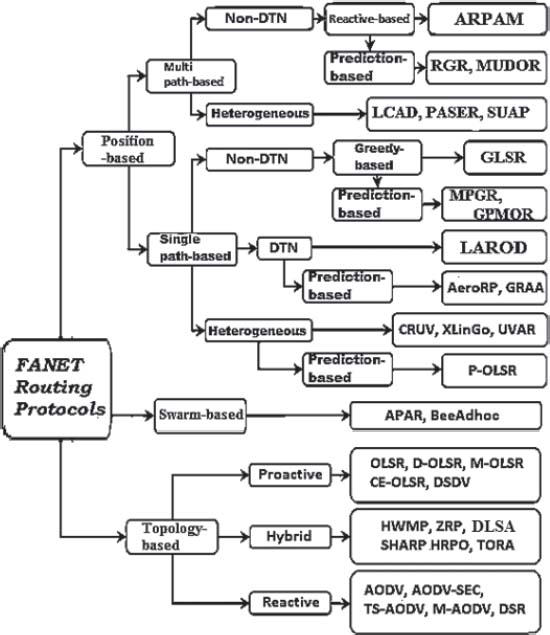
Figure 2: Classification of Routing Protocol for FANET (Nugroho et al., 2015)
In (Nugroho et al., 2015) researchers used the differential geometry to design the guidance system with the capability of target tracking and rendezvous with UAVs. The idea of velocity factors of UAVs and targets is presented by researchers with a mathematical solution. In the research paper (Oh et al., 2014) the design for UAVs of a cooperative localization mechanism is presented by using the non-parameterized belief algorithm. The authors consider dynamic variables for task allocation in terms of the position of UAVs in a predefine ambit. Authors (Park & Corson, 1998) proposed a framework using UAVs for cooperative searching. Reliability and movement planning are used as determination parameters for cooperative task allocations while governing tasks performed by the framework with motion planning and their control. Unlike traditional networks, the study of swarm organizing can be developed from nature. The nature-based biological inspired algorithms changed the model of networking in the field of biological behavior for the optimal solution (Pei et al., 2000).
3. Biologically Inspired Algorithms
Bio-inspired computing-based techniques are gaining importance in the current engineering research domain, particularly for solving complex optimization problems. These are stochastic search techniques which are developed to achieve near-optimal solutions to large-scale optimization problems. The conventional mathematical optimization methods often fail as the solutions are trapped in local optima, which gave rise to the development of alternate derivative free metaheuristic global optimization techniques. In recent times, the bio-inspired algorithms have been explored for various applications and their performance is as good as or better than that of conventional techniques. In this study, two biologically inspired algorithms are proposed with comparative and performance based analysis to check the effectiveness and better performance. Each algorithm has its own feature and efficiency. The two main inspired algorithms are here discussed that are BCO and MAA (Figures 3 and 6, respectively). The details of these schemes are given in the subsequent sections.
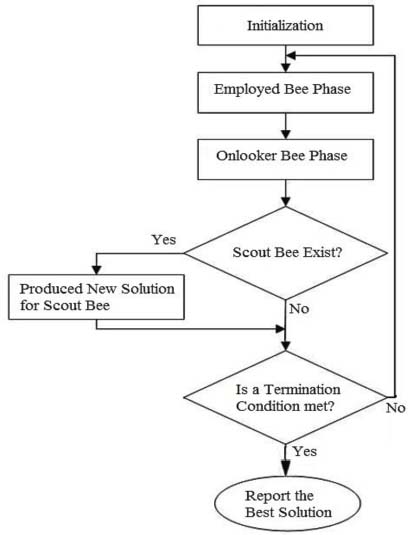
Figure 3: Algorithm of BCO
3.1. Bee Colony Optimization (BCO) Algorithm
The best adaptive algorithm is the Bee colony algorithm when dealing with topology changes. Bee optimization algorithm differs from some conventional routing algorithms used for routing in telecommunication networks. Alike to other swarms’ algorithm, the algorithm of bee started to collect the data and transmitted to other nodes. Figure 4 shows the bee colony behavior diagram. By nature, the beehive operational principles are predefining for the allocation of responsibilities among the bees. In Figure searching begins with an employed bee for a nectar source while other bees (onlookers) remain in the hive and receive the data only from employed bees by using special “waggle dance”. This waggle dance devolves on the sun’s location. The motion of a bee dance strongly indicates to the other bees where the precisely targeted food source is located.
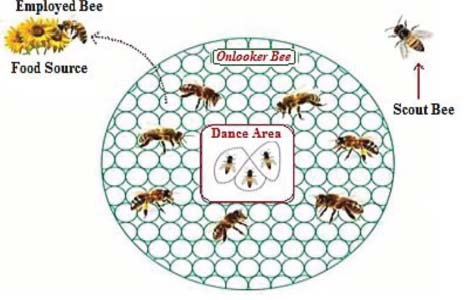
Figure 4: Bee colony behavior in wildlife
In (Sahingoz, 2014) checking the scout characteristics of every visited node the conclusion of route efficiency can be drawn by the algorithm. The probabilistic calculation is maintained by a probability distribution table. These are complex procedures that require several verification steps. Such things happen as if more than one forward scout is received by a node. It confirmed it first that either the scout with the same ID has arrived before or not, the next important unit is forager-bees come in action after the culmination of scout process and route conclusion. The foragers transfer the information like a real bee carries the food (Tareque et al., 2015). The number of foragers played an important role in the route calculation using dance formula phenomena and then the phase of resource foraging started.
3.2. Moth-and-Ant (MAA) Algorithm
The male moth has a peculiar trajectory for light source because during searching it observed the direction of light origin with its natural capability of piercing thermal sensing to locate a direction. The natural behavior of the moth-ant shows in Figure 5. Initially, it follows a straight line by using dive speed to reach the target quickly. In the second step when it senses that the target is near, it slowdowns its speed and cautiously flies in the direction of the target, and follows the zigzag curve. Finally, the moth feels that the light source is closer than a circular fly is used to lock the source. This pattern deal with the low-level routing of the network based on the ant`s chemical trail for maintenance rule to follow the trajectory of the commander node. Hence this scenario minimizes the delay. Similarly, ants use a striking chemical to record the trajectory to leave the path to their partner where they can promptly find the source of food such a feature refer to the time decay property (Figure 6).
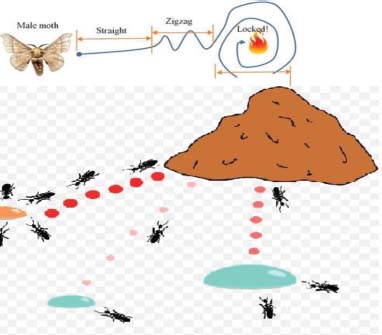
Figure 5: The performance illustration of MAA algorithm
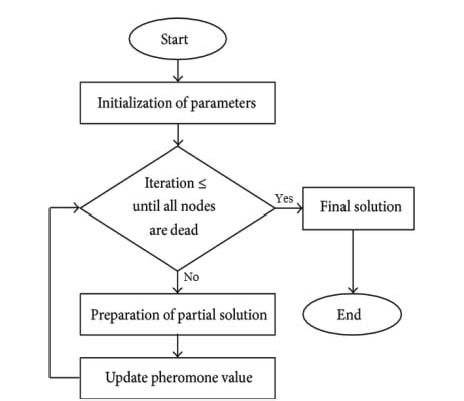
Figure 6: Algorithm of MAA
Three levels of networks for routing protocols are high-level network, low-level network, and cross-level presented in (Pei et al., 2000) and exploited the directional antennas for the multi-beam of the hierarchical network. Considering long space links and a high rate of communication a fence routing protocol exploits the effectual benefits in a high level of multi-beam antennas network with higher throughput and lower delay in competitive to traditional protocols. Moth-inspired routing is capable of low-level networks with high density and short distances. Low rate link overcomes the singular mobility of sink in terms of less packet loss and higher throughput than traditional mobile routing protocols. A MAA behavior has high throughput and low latency and in routing for cross-level this protocol ensures the approaching chance to the commander node.
4. Performance Analysis of BCO and MAA
The performance of BCO and MAA has performed by using MATLAB tool. For the performance evaluation the proposed parameters are Packet Delivery Ratio (Figure 7), End to End Delay (Figure 8), Transmission Loss and Network Lifetime (Figure 9). FANETs increase in the quantity of UAVs will result in a decrease in the number of tasks per UAV. Moreover, the increase of UAV in the network handles more tasks cooperatively but caused high latency. BCO offered the lowest network cooperation time than Moth-ant. Packet data routing delivery in FANETs may be used as biologically inspired algorithms. These are only for routing purposes but are not suitable and efficient for task optimization. An increase in the number of nodes within the targeted area may increase the throughput of the protocols. BCO is the most adaptive algorithm in topology change situations. Quickly adjust to the changes with the rate increase and show the best throughput values. BCO has a longer delay because of the search for a new route to the destination node (Figure 10). Ant-HocNet protocol performed efficiently in the FANETs environment. This protocol has fine scalability and the same as BCO the throughput of these protocols increases as the number of nodes increases. When the node rate slightly changes in rate, the heavy load due to routing overhead with an increase in node mobility remains the throughput level at the same position but protocols are not subject to heavy loads in this regard. Both methods appear more effective in comparison to other biologically inspired methods and are used for data delivery and routing but not good enough for the problem of task optimization.
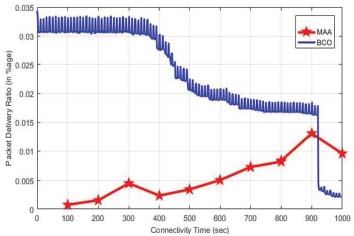
Figure 7: PDR of MAA and BCO
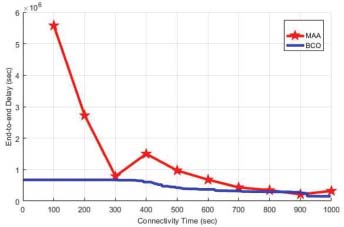
Figure 8: E2ED of MAA and BCO
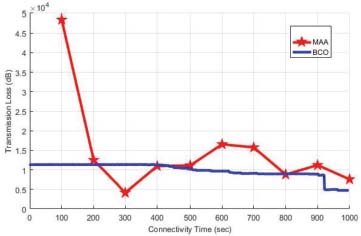
Figure 9: Transmission Loss of MAA and BCO
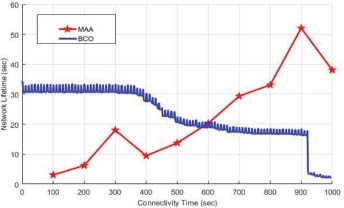
Figure 10: Network Lifetime of MAA and BCO
MAA inspired at a low speed can achieve better performance due to the construction of non-optimal paths comparative to traditional mobile routing. Moth routing has significant throughput as compared to traditional protocols. Sink speed of moth increases as a result of an increase in throughput in low-level routing. Ant- inspired to validate the cross-level routing scheme. It has also better scalability but has high packet loss when dealing with cross-level routing. This optimization is good for cooperative task allocation in FANET and can obtain cooperatively task allocation and rendezvous. Time and intricate cooperative problems in FANETs are reduced by this algorithm. we summarize different algorithms as discusses above and summarizes their features and limitations in the FANET scenario.
From the given scenarios it has been clearly revealed that each algorithm has the impact based performance in which each has given different results from simulation perspective. The main reason is that each algorithm follows a specific approach to route the data from one perspective node to another by using the alternative path.
Features of Bee Colony Algorithm are following:
• The algorithm has better throughput than DSR and DSDV.
• It may be used in packet routing in FANET.
• Bee Ad-Hoc increase in proportion to the increase of the amount of the node.
• It is the most adaptive algorithm in topology changes.
• Quickly adjust to the changes with the rate increase and show the best throughput values.
• Nodes increases cause an increase in the throughput.
• Alike DSDV and DSR this algorithm is good as routing and throughput.
Features of Moth-and-Ant routing algorithms.
• Moth routing has significant throughput as compared to traditional protocols.
• Sink speed of moth increases as a result of an increase in throughput in low-level routing.
• Smaller the updating period brings a higher throughput.
• Ant- inspired to validate the cross-level routing scheme.
• It has better scalability.
• Moths inspired at low speed achieve good performance.
5. Conclusion
Routing and task allocation have unique requirements, especially when dealing with FANETs. Aspects may be considerable to find the most efficient route, controlling the latency, ensuring the reliability, allowing the network to scale, and ensure the QoS. The design of suitable protocols and algorithms in FANET is a complex task due to its high mobility and dynamic changes in topology. High node addition and removal behavior still see native protocols in FANET. In this article, we attempted to explain the research area based on biologically inspired algorithms. The reason to undertake this important survey is due to only a few surveys focusing on the naturally inspired fields. We discussed six categories of routing protocols and perceived their applicability in FANETs. Further, different techniques of biologically inspired are discussed and see the extent to which they are suitable for FANETs. From this survey, it has been revealed that the main and major issue in FANET is routing due to the high mobility of UAVs. From simulations it has been revealed that BCO and MAA has a great impact on the performance regarding the PDR, E2ED, Transmission Loss and Network Lifetime. Each algorithm has given best results based on the proposed scenario in perspective of simulations. Research work in this area is still in infancy and it is a hot area for researchers.
In the future, there are many issues and challenges in this network that properly needs to be fixed and design some efficient and reliable routing algorithms that maintain the possible and effective communication channels between the UAVs to UAVs and with the ground stations. Due to the flying nature of the UAVs, the energy consumption is also a major issue in this network for which robust routing algorithms are required by using the residual energy approach in which the network stability period can be measured. Also, link stability is the most and major issue because due to the high speed of the UAVs the link stability is the major issue because of the high speed of UAVs there occurs path loss and transmission loss for which routing protocols need to be designed.
Authors’ contributions: All the authors contributed to this research.
Conflicts of Interest: The authors declare that they have no conflicts of interest.
References
Ahmed, S. (2020). Nature Inspired Optimization Techniques, a review for FANETs. Sukkur IBA Journal of Emerging Technologies, 3(2), 40–58.
Alshbatat, A. I., & Dong, L. (2010). Cross layer design for mobile ad-hoc unmanned aerial vehicle communication networks. 2010 International Conference on Networking, Sensing and Control (ICNSC),
Bekmezci, I., Sahingoz, O. K., & Temel, Ş. (2013). Flying ad-hoc networks (FANETs): A survey. Ad Hoc Networks, 11(3), 1254-1270.
Bekmezci, I., Sen, I., & Erkalkan, E. (2015). Flying ad hoc networks (FANET) test bed implementation. 2015 7th International conference on recent advances in space technologies (RAST),
Billington, J., & Yuan, C. (2009). On modelling and analysing the dynamic MANET on-demand (DYMO) routing protocol. In Transactions on Petri Nets and Other Models of Concurrency III (pp. 98–126). Springer.
Bujari, A., Palazzi, C. E., & Ronzani, D. (2017). FANET application scenarios and mobility models. Proceedings of the 3rd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications,
Cheng, C.-M., Hsiao, P.-H., Kung, H., & Vlah, D. (2007). Maximizing throughput of UAV-relaying networks with the load-carry-and-deliver paradigm. 2007 IEEE Wireless Communications and Networking Conference,
Dhurandher, S. K., Misra, S., Pruthi, P., Singhal, S., Aggarwal, S., & Woungang, I. (2011). Using bee algorithm for peer-to-peer file searching in mobile ad hoc networks. Journal of Network and Computer Applications, 34(5), 1498–1508.
Flury, R., & Wattenhofer, R. (2008). Randomized 3D geographic routing. IEEE INFOCOM 2008-The 27th Conference on Computer Communications,
Forsmann, J. H., Hiromoto, R. E., & Svoboda, J. (2007). A time-slotted on-demand routing protocol for mobile ad hoc unmanned vehicle systems. Unmanned Systems Technology IX,
Frew, E. W., & Brown, T. X. (2009). Networking issues for small unmanned aircraft systems. Journal of Intelligent and Robotic Systems, 54(1), 21–37.
Haas, Z. (1998). The zone routing protocol (ZRP) for ad hoc networks. IETF Internet draft, draft-ietf-manet-zone-zrp-01. txt.
Jacquet, P., Muhlethaler, P., Clausen, T., Laouiti, A., Qayyum, A., & Viennot, L. (2001). Optimized link state routing protocol for ad hoc networks. Proceedings. IEEE International Multi Topic Conference, 2001. IEEE INMIC 2001. Technology for the 21st Century.,
Kaddoura, M., Trent, B., Ramanujan, R., & Hadynski, G. (2011). BGP-MX: Border gateway protocol with mobility extensions. 2011-MILCOM 2011 Military Communications Conference,
Karaboga, D. (2005). An idea based on honey bee swarm for numerical optimization.
Karp, B., & Kung, H.-T. (2000). GPSR: Greedy perimeter stateless routing for wireless networks. Proceedings of the 6th annual international conference on Mobile computing and networking,
Kim, D.-Y., & Lee, J.-W. (2017). Topology construction for flying ad hoc networks (FANETs). 2017 International Conference on Information and Communication Technology Convergence (ICTC),
Ko, Y. B., & Vaidya, N. H. (2000). Location‐Aided Routing (LAR) in mobile ad hoc networks. Wireless networks, 6(4), 307–321.
Kuperman, G., Veytser, L., Cheng, B.-N., Moore, S., & Narula-Tam, A. (2014). A comparison of OLSR and OSPF-MDR for large-scale airborne mobile ad-hoc networks. Proceedings of the third ACM workshop on Airborne networks and communications,
Leonov, A. V. (2016). Application of bee colony algorithm for FANET routing. 2016 17th International Conference of Young Specialists on Micro/Nanotechnologies and Electron Devices (EDM),
Lidowski, R. L., Mullins, B. E., & Baldwin, R. O. (2009). A novel communications protocol using geographic routing for swarming uavs performing a search mission. 2009 IEEE International Conference on Pervasive Computing and Communications,
Liu, C., & Wu, J. (2009). Efficient geometric routing in three dimensional ad hoc networks. IEEE INFOCOM 2009,
Nugroho, D. A., Prasetiadi, A., & Kim, D.-S. (2015). Male-silkmoth-inspired routing algorithm for large-scale wireless mesh networks. Journal of Communications and Networks, 17(4), 384–393.
Oh, H., Turchi, D., Kim, S., Tsourdos, A., Pollini, L., & White, B. (2014). Coordinated standoff tracking using path shaping for multiple UAVs. IEEE Transactions on Aerospace and Electronic Systems, 50(1), 348–363.
Park, V., & Corson, S. (1998). Temporally-ordered routing algorithm (TORA) version 1 functional specification (Internet-draft). Mobile Ad-hoc Network (MANET) Working Group, IETF.
Pei, G., Gerla, M., & Chen, T.-W. (2000). Fisheye state routing: A routing scheme for ad hoc wireless networks. 2000 IEEE International Conference on Communications. ICC 2000. Global Convergence Through Communications. Conference Record,
Pham, D. T., Ghanbarzadeh, A., Koç, E., Otri, S., Rahim, S., & Zaidi, M. (2006). The bees algorithm—a novel tool for complex optimisation problems. In Intelligent production machines and systems (pp. 454–459). Elsevier.
Sahingoz, O. K. (2014). Networking models in flying ad-hoc networks (FANETs): Concepts and challenges. Journal of Intelligent & Robotic Systems, 74(1), 513–527.
Tareque, M. H., Hossain, M. S., & Atiquzzaman, M. (2015). On the routing in flying ad hoc networks. 2015 federated conference on computer science and information systems (FedCSIS).
Author’s Biography

Altaf Hussain received his B.S and M.S degrees in Computer Science from University of Peshawar, Pakistan (2013) and The University of Agriculture Peshawar, Pakistan (2017) respectively. He worked at The University of Agriculture as a Student Research Scholar from 2017-2019. During his MS Degree he has completed his research in Computer Networks especially in Routing Protocols in Drone Networks. His recent approach is PhD in Computer Science & Technology. He has served as a Lecturer in Computer Science Department in Govt Degree College Lal Qilla Dir L, KPK Pakistan from 2020-2021. He has published many research papers including survey/review and conference papers. He was Research Scholar in (Career Dynamics Research Academy) Peshawar, Pakistan for one and a half year. Currently, he is working as a Research Assistant with the Department of Accounting & Information Systems, College of Business and Economics, Qatar University. His research interest includes Wireless Networks, Sensor Networks, Radio Propagation Models, and Unmanned Aerial Drone Networks.

Habib Ullah Khan is working as a Professor of Information Systems in the Department of Accounting & Information Systems, College of Business and Economics, Qatar University. He completed his Ph.D. degree in Management Information System area from Leeds. Beckett University, UK. Academic experience-wise he was associated with many leading universities of Gulf, USA, and Europe. Overall he has more than twenty years of working and research experience in different multinational companies (on different managerial positions), and reputed educational institutions in UK, USA, Oman, UAE, Saudi Arabia, and Qatar. During his past experience, he was an excellent team player and leader; his diversified experience helped him to manage multicultural students and the workforce in educational institutions.

Shah Nazir is working as Assistant Professor/HOD of Computer Science in Department of Computer Science in University of Swabi, Swabi Pakistan. He completed his PhD degree in Software Engineering from University of Peshawar Pakistan. He has published many research articles as well as review and conference papers. His research interest includes Software Engineering, Component Based Software Engineering, Fuzzy Logic, Analytic Hierarchy/Network Process, Systematic Literature review & Software Birthmark.

Tariq Hussain received his MS and BS Degrees in Information Technology from the Institute of Computer Sciences and Information Technology the University of Agriculture Peshawar, Pakistan (2019), and University of Malakand, Pakistan (2015) respectively. He has published many research papers in Computer Networks. Currently he is a Doctoral Student at School of Computer Science and Information Engineering, Zhejiang Gongshang University China. His research interests are the Internet of Things, 3D Point Cloud, Big Data, Data analytics and AI.

Ijaz Ullah is working as a visiting Lecturer with the Department of Computer Science, University of Swabi, Swabi Pakistan. He has completed his Bachelor degree in Computer Science from University of Peshawar, Pakistan and Master Degree from EIT Digital Mster School. EIT Digital Master School provides dual degrees. So, he got Master in Cloud Computing from University of Rennese 1 France and ICT Innovation degree from Technical University of Berlin Germany. His research interest includes Cloud Computing and Networks.